Table of Contents
Data security guide for members
ArtsPool takes data security very seriously, and we ask that all members work with us to keep your organization’s information safe. Security is a team effort that only works when all team members com…
ArtsPool takes data security very seriously, and we ask that all members work with us to keep your organization’s information safe. Security is a team effort that only works when all team members commit to good security hygiene.
For more information on ArtsPool’s internal data security practices, see the Data Security Policy.
General security
The best place to start when thinking about data security is to take some time to master basic practices for staying safe online. The articles, guides, and tools below are good places to start.
Firefox Monitor: Security tips to protect yourself from hackers
The 5 Habits of Practically Unhackable People
Password Security: How to Avoid the Most Common Password Mistakes
Have I Been Pwned? Check if your password has been compromised in data breaches.
Password security
When sharing passwords and personally identifiable information (social security numbers, home address, favorite pet), we ask that you follow the golden rule of ArtsPool:
Thou shalt not send passwords or personally identifiable information over email or store them in Google Drive. Instead, share the info with us via our shared password manager, send it to us via a secure file transfer system such as DropSecure, or call us.
In addition to security around sharing passwords, below are some other considerations to keep in mind when thinking about your passwords.
Password uniqueness
Whenever possible, use a unique random password for every account. You can generate random passwords using the password generator tool in most password managers or via tools such as xkpasswd.net or useapassphrase.com that allow for customization. In particular, it is very important that you NEVER use the same password for your password manager and your email account. These two services are gatekeepers to many other services, so using the same password could result in you completely losing access to all of the keys to your kingdom.
Two-factor authentication
Two-factor authentication (2FA) is a feature on certain systems that will ask you for a secondary code when logging in. It is a good idea to enable 2FA using an authenticator app such as Google Authenticator or Authy whenever it is available. SMS text message 2FA is available on some systems, but it is not secure and should only be used if an app-based option is not available. For more on why text message codes are a security risk, see “Criminals Can Steal Your Phone Number. Here’s How to Stop Them.”
If your organization uses Google Apps for its email and document management, follow the guide below to activate 2FA on your Google Account.
Google 2-Step Verification Guide
Microsoft two-step verification guide
Password rotation
It is a best practice to rotate your passwords regularly, particularly for sensitive accounts such as your email account, your password manager, and any accounts associated with your company or personal finances. This can be stressful if you are used to keeping all of your passwords in your head, but it’s a piece of cake if you use a password manager to remember your passwords.
Saving passwords in your browser
Don’t save passwords in your browser unless the password is not sensitive or the password has 2FA enabled. Use your password manager instead.
What to do if your passwords are compromised
If you have reason to believe that a password is compromised:
- Immediately change the affected password.
- If the password you believe is compromised is the password to your password manager, also change your passwords for your email, document storage, payroll account, and any other system that may grant access to sensitive information.
- If the password is for an account used to authenticate third party apps (e.g. Google Apps, Xero, Slack, etc), be sure to also revoke access to any applications that may be using your Google account for authentication and re-authenticate them. More info: Manage connections between your Google Account and third-parties.
- Report the incident and the steps you took to the person at your organization who manages information technology, security, or operations.
Document security
Document storage
Personally identifiable information
Per ArtsPool's Data Security Policy, you should not store Social Security numbers and bank information permanently in ArtsPool's Google Drive folders. Instead, use other tools such as the ArtsPool app, a secure file transfer tool such as DropSecure, or Tax1099 to collect or send this data. Store the information in the system where it is needed rather than in Google Drive.
Restricted folders and files
Be careful to review permissions regularly on any folders such as employee folders that may contain personally identifiable information or other sensitive employee data. Individual employee folders should only be accessible by the employee or independent contractors themselves, their hiring manager, and authorized senior staff (Executive Director, etc). Similarly, if a budget document contains employee compensation data, take appropriate steps to restrict access to that information to employees who are authorized to see employee compensation (e.g., by adding protection to the individual spreadsheet tab or by restricting access to the document itself).
Time-based sharing in Google Drive
When sharing a document with an external user (someone who doesn’t have an email address associated with your organization or ArtsPool), it’s a good practice to set an access expiration date so that the user’s access will automatically expire after a certain amount of time. To do this in Google Drive:
- Right-click the document and select Share.
- Enter the person’s email in the Add people... field.
- From the Role dropdown menu, confirm the appropriate role and select Add expiration.
- Update the access expiration by clicking the pencil icon.
- Add a Message if needed.
- Click Send.
Digital signatures
If your organization uses DocuSign or a similar system for digital signatures, do not use that system to permanently store the signed documents. When a document is signed, download it and store it in an appropriate folder in Google Drive or other document storage system, renaming the document if necessary to allow for easy access via search. Once it is stored in your document storage system, you can delete the document from the digital signature system. Automation tools such as Zapier, Workato, and IFTT or built-in integrations for Google Drive, Dropbox, etc. can help automate this process.
Be careful of using digital signature systems to get signatures on any documents that contain personally identifiable information. Many of these systems send notifications to signers or cc: recipients contain PDFs of the document, which could potentially expose personally identifiable information if any of the recipients’ email were to be compromised.
Device security
Screen Locks
To prevent unauthorized access to your device when you are not directly in front of it, set your device to lock its screen and required a password after a certain period of inactivity (preferably a short period of time). Even with a screen lock turned on, it is a best practice to lock your screen when you walk away from your computer for a significant amount of time.
Mac OS
Screen lock settings for Mac OS can be found in System Settings > Lock Screen. Set the device to require a password immediately after sleep or screen saver begins, and set your screensaver to start after 5 minutes or less.
Android
To set a device lock passcode, pattern, or password on an Android device, see the article Set screen lock on an Android device.
iOS
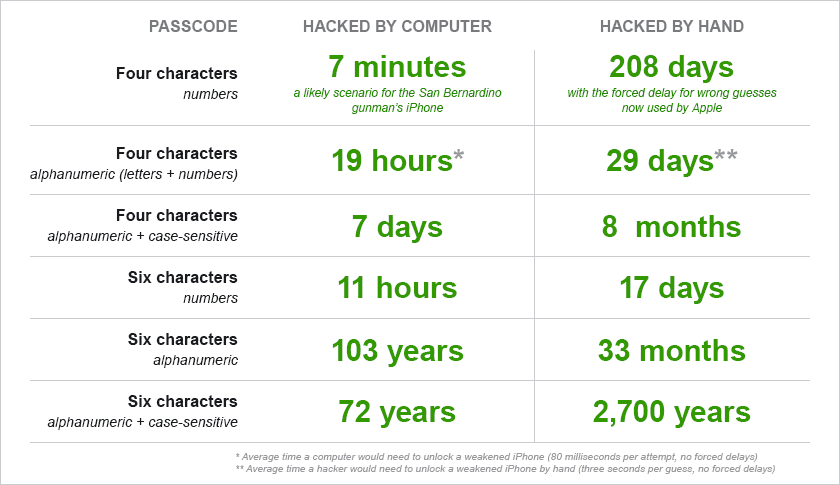
On iOS, you can set a longer passcode by setting a custom alphanumeric code.
- Launch Settings.
- Tap Face ID & Passcode (or Touch ID & Passcode).
- Enter your existing 4-digit or 6-digit passcode, if you have one.
- Tap Change Passcode.
- Re-enter your existing passcode if you have one.
- Tap Passcode Options.
- Tap Custom Alphanumeric Code
- Enter your new alphanumeric password.
- Re-enter your new alphanumeric password.
Windows
- Go to Control Panel > Appearance & Personalization > Change screen saver
- Check the box for On resume, display logon screen.
- Set a time for how long your PC should wait before starting the screen saver.
Anti-malware
Anti-malware software is an important part of your online security since it helps to protect your computer against viruses, ransomware, keyloggers, phishing, and other malicious activities that might be attempted by people lurking in the shadows of the internet. Be sure that anti-malware software is installed on all machines and instruct staff should keep the software running at all times.
Many internet service providers provide a free license for antimalware software as part of your subscription (e.g. Optimum provides a McAfee license), so if you have a personal computer that you use occasionally for work, consider activating this license if you have access to one.
Track your device
Many devices allow you to track the location of the device if it is lost or stolen. This can provide valuable information if you need to file a police report. Below are links to set this up on a few different systems:
Apple: Find my iPhone/iPad/Watch/Mac
Windows: Find and lock a lost device
What to do if a device is stolen/lost
If you have a screen lock on your device, are in the practice of locking it when you walk away from your computer, and don’t save data on your hard drive, you already have a first line of defense. However, this is not a 100% guarantee that a determined attacker can’t compromise your accounts. If you discover that a device is lost or stolen, immediately take the following steps:
- Notify the person at your organization who manages information technology, security, or operations. If your organization uses Google Apps, they should be able to reset your Google Apps sign-in cookies, wipe Google data on mobile devices if necessary, and revoke access to third-party accounts that use Google for sign-in. They can also file a police report or insurance claim if necessary.
- Reset your email password.
- Reset your password manager password.
- Reset any other sensitive passwords (or ALL passwords if you are paranoid).
- If the device is a mobile device, visit the websites of apps you use regularly and reset as many passwords as you can.
- Reset any other passwords for accounts that you may have been logged into at the time of the loss or theft (e.g. bank accounts, etc).
- If the device is a mobile device, let your cellular carrier know and ask them to deactivate it for you.
How to stay safe online
As cloud-based technology becomes more and more integrated into our work and personal lives, it is even more important to utilize safe practices on the internet. There are a few things that you can look out for to reduce your risk online.
Use encrypted connections
Be wary of websites that don’t use encrypted connections between your browser and their servers as they could expose information to “man in the middle” attackers in transit. The easiest way to check for this is to look at the address bar of your browser. If it uses https (s for “secure”) then the website is using an encrypted connection with an SSL (Secure Socket Layer) certificate. Most browsers will display a lock or message indicating that the website is secure to the left of the web address. Don’t want to always check whether websites are using HTTPS? The Electronic Frontier Foundation has developed a great browser extension called HTTPS Everywhere to encrypt your web traffic even if the web site doesn’t use HTTPS.
Use a VPN on public wifi networks
When transmitting sensitive data on a public wifi network such as at a cafe, on a train, or at an airport, it’s a good idea to use a Virtual Private Network, or VPN, since it provides an extra layer of protection when your network connection could be potentially compromised. It may not be feasible to require staff to use VPNs at all times, but it’s a good idea to consider security when choosing a network to connect to and to turn on a VPN (if you have one) if you want added security. Some anti-malware comes with a built in optional VPN service, while others offer it as an add-on service. Some reputable stand-alone VPNs are Nord VPN and Mullvad VPN.
Malicious emails
Malicious emails are emails that may look legitimate, but are a way for the sender to get confidential information from the recipient. Here are a few ways to recognize if an email might be malicious:
- It needs you to act quickly (e.g. account compromised, order fulfillment)
- The sender’s address is not correct. For example, if an email comes from the domain @acme-arts.com and not the expected @acme-arts.org, it is signal that you should proceed with caution and confirm that the email is legitimate before acting on it.
- Embedded links in the email have strange addresses. Without clicking on the link, hover over it and a small pop-up (usually at the bottom left of your window) will show you the web address that the link points to.
- The language, spelling, and grammar are off. Of course, a legitimate email can have typos, but if there are major inconsistencies, be wary.
If you’re not sure if an email is malicious, you can contact the sender’s company directly using a legitimate source of information that is not the actual email (i.e. contact information from the company’s website). Another way to check is by searching for the company online, but do not use any information that is provided in the email for your search.
Spam
Spam is just another way of saying “junk mail.” They tend not to be malicious, but can be bothersome to your work if your inbox continues to get filled up with them. The tips below can help reduce how much spam you get:
- Enable filters. To do this in Gmail, go to Settings - Filters & Blocked Addresses and select Create a new filter.
- Report the email as spam when it shows up in your inbox.
- Avoid displaying your email address on online profiles and social media sites.
Phishing
Phishing is a fraudulent attempt to collect personal information, financial information, and/or infect a computer with malware via email or malicious websites. A dedicated attempt on specific targets is called spear phishing. An example of this is when an attack is made to gain access to a business’ customer list. Once the list is obtained, another attack is made on the customers, which looks more legitimate due to the use of the customer list.
Here are additional tips to help you stay safe:
- Do not reveal personal or financial information in an email, and do not respond to solicitation for such information.
- Check any website’s security before sending/entering sensitive information. The URL is helpful for this; if you see it start with “https” or has a lock icon next to it, it’s a sign that the communication of data between you and the site is secure and encrypted.
- Keep your software up-to-date on internet-connected devices. This is particularly important for your anti-malware.
Reporting Attacks
If you are a victim of an online attack, report it right away to the person at your organization who manages information technology, security, or operations. If you believe that financial information was compromised, contact the financial institution immediately, and keep an eye out for unauthorized charges on any financial accounts. Depending on the severity of the compromise, consider reporting the attack to local law enforcement agencies.
Resources
How did we do?
Security on macOS
